Advertisement
Databases don’t just hold data—they defend it. In SQL, building tables and writing queries is only part of the job. You also need to control who can access or change what’s inside. That’s where Grant and Revoke come in. These commands act like gatekeepers, managing who can read, update, insert, or delete data.
For developers, administrators, or anyone managing systems, understanding Grant and Revoke in SQL is key to keeping things secure and efficient. This article breaks it all down simply—how permissions work, why they matter, and how these commands help you manage access with clarity and control.
In SQL, data access isn’t something you want to leave to chance. Every database has rules about who can do what—and those rules are enforced through permissions. If someone wants to read a table, insert a record, or modify a view, they need explicit permission. That’s where the GRANT and REVOKE commands step in. These two commands are the tools that database administrators use to control access, set boundaries, and maintain order.
GRANT is used to hand out specific rights to a user or role. Think of it as saying, “Yes, you’re allowed to do this.” For example:
GRANT SELECT, INSERT ON employees TO john_doe;
This gives john_doe the ability to view and add data to the employee's table. If you later change your mind, REVOKE pulls those rights back:
REVOKE INSERT ON employees FROM john_doe;
Now, john_doe can still read but can't insert new records.
The beauty of these commands lies in their simplicity and precision. You can give access to access at numerous levels—whole tables, particular columns, whole schemas, or even stored procedures. But with that accuracy comes a responsibility. Over-granting can be dangerous, and under-granting can create workflow problems. Balancing access is key to effectively managing database user permissions—and that's exactly what GRANT and REVOKE help you do.
Picture an online store where your database holds everything from products to customer payments. If every developer or application has equal access, you're setting the stage for disaster. Permission management isn’t just about blocking mistakes—it’s about creating a secure, structured environment.

Understanding Grant and Revoke in SQL supports the principle of least privilege. Users only get access to what they truly need, reducing the risk of unauthorized edits, deletions, or data leaks. It’s like giving a developer access to inventory data—but not payment records.
Role-based access is another strength. Instead of managing individual users, you assign roles like “report_viewer” for read-only access or “data_entry” for updating records. It streamlines both onboarding and auditing.
Speaking of audits, defined permissions make tracing user actions easier. If something goes wrong, you know where to look.
Lastly, managing database user permissions plays a vital role in regulatory compliance. Industries like healthcare and finance demand transparency in access control, and SQL’s permission system helps meet those standards effectively.
Using the GRANT and REVOKE commands effectively does more than just control access—it strengthens your database design. Why? Because it forces you to consider access rights during the planning stage, not after the fact.
Consider a hospital database. You’d define roles like doctors, nurses, and receptionists—each needing different access levels. Doctors might read medical records, while receptionists see only names and appointment times. Assigning these permissions explicitly using GRANT makes your schema self-explanatory and role-aware.
Some systems, like PostgreSQL, support cascading permissions using WITH GRANT OPTION. For example:
GRANT SELECT ON lab_results TO dr_smith WITH GRANT OPTION;
Now, dr_smith can share that access. It’s useful but risky—permissions can spread unintentionally if not monitored.
REVOKE can remove both direct and inherited access. This gives you the flexibility to tailor exceptions without dismantling roles entirely.
Finally, granular control improves system architecture. Frontend and backend services can connect through separate users with distinct permissions, reducing the risk if one component is compromised.
In essence, understanding Grant and Revoke in SQL means designing your systems with clarity, security, and intent from day one.
Let’s ground this in reality. Say you're working on a content management system for a news website. You might create different users like editors, contributors, and viewers. Editors can publish and update articles, contributors can submit drafts, and viewers can only read. This is a textbook example of managing database user permissions through GRANT.

You might run:
GRANT INSERT, UPDATE ON articles TO contributor;
GRANT SELECT, UPDATE, DELETE ON articles TO editor;
However, real-life situations often introduce complexity. Maybe someone gets promoted, and you forget to revoke their old permissions. Or you accidentally grant write access to a sensitive table like user_credentials. This is why permission reviews are important. Periodic audits help catch mistakes before they become security incidents.
Another common trap is granting permissions directly to individuals instead of roles. This leads to what’s called "permission sprawl"—a situation where you have dozens of users with overlapping, unclear access rights. When someone leaves the company, you end up hunting down every individual permission they had, which is error-prone.
Always aim to define roles first, grant permissions to those roles, and assign users to roles. If someone changes jobs, you just switch their role. Cleaner, safer, and easier to manage.
Be cautious with inherited permissions and cascading grants—they can unintentionally extend access. Always test permission changes in a staging environment first. A simple mistake in a REVOKE command could either expose sensitive data or restrict critical access without warning.
Getting a firm grip on who can do what in your database is key to both security and efficiency. By understanding Grant and Revoke in SQL, you can define clear access rules and avoid messy permission issues down the road. These commands aren't just about locking people out—they're about giving the right access to the right users at the right time. With careful use, they help ensure your system runs smoothly, securely, and with accountability baked in.
Advertisement
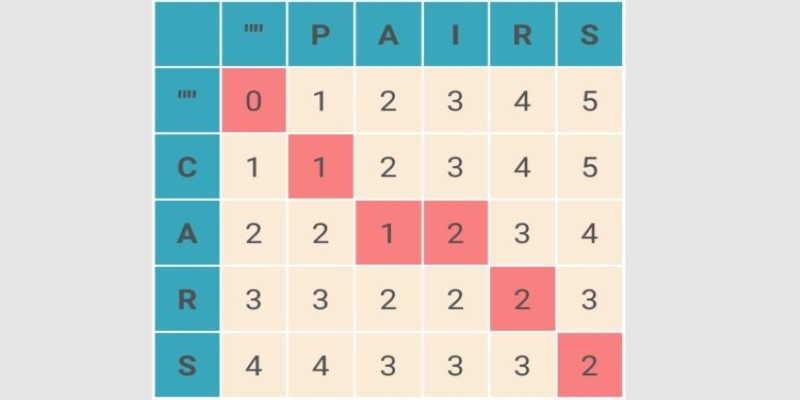
What Levenshtein Distance is and how it powers AI applications through string similarity, error correction, and fuzzy matching in natural language processing

Gemma Scope is Google’s groundbreaking microscope for peering into AI’s thought process, helping decode complex models with unprecedented transparency and insight for developers and researchers
How the SUMPRODUCT function in Excel can simplify your data calculations. This detailed guide explains its uses, structure, and practical benefits for smarter spreadsheet management

How the ElevenLabs API powers voice synthesis, cloning, and real-time conversion for developers and creators. Discover practical applications, features, and ethical insights

Learn Apache Storm fundamentals with this detailed guide covering architecture, key concepts, and real-world use cases. Perfect for mastering real-time stream processing at scale

Learn how process industries can catch up in AI using clear steps focused on data, skills, pilot projects, and smart integration

Find out the Top 6 Humanoid Robots in 2025 that are transforming industries and redefining human-machine interaction. Discover how these advanced AI-powered robots are shaping the future of automation, customer service, and healthcare

Understand the Difference Between Non Relational Database and Relational Database through clear comparisons of structure, performance, and scalability. Find out which is better for your data needs

Wondering whether to use Streamlit or Gradio for your Python dashboard? Discover the key differences in setup, customization, use cases, and deployment to pick the best tool for your project

How self-driving tractors supervised remotely are transforming AI farming by combining automation with human oversight, making agriculture more efficient and sustainable

What Hannover Messe 2025 has in store, from autonomous robots transforming manufacturing to generative AI driving innovation in industrial automation

How the Chain of Verification enhances prompt engineering for unparalleled accuracy. Discover how structured prompt validation minimizes AI errors and boosts response reliability